From the
International Herald Tribune via the
Common Dreams NewsCenter an interesting article by Hans Blix, the former chief UN weapons inspector.
During the Cold War, it proved possible to reach many significant agreements on disarmament. Why does it seem so impossible now, when the great powers no longer feel threatened by one another? Almost all the talk these days is about the proliferation of weapons of mass destruction to states like Iran and North Korea, or to terrorists. Foreign ministers meet again and again, concerned that Iran has enriched a few milligrams of uranium to a 4 percent level.
Some want to start waving the stick immediately. They are convinced that Iran will eventually violate its commitment under the Nuclear Nonproliferation Treaty to forego nuclear weapons.
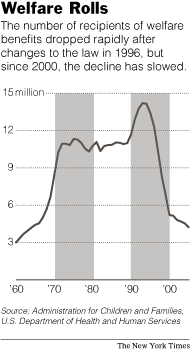
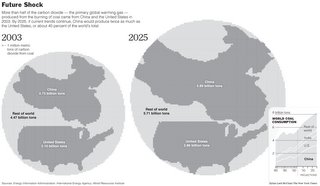
While it's desirable that the foreign ministers talk about Iran, they don't seem to devote any thought to the fact that there are still some 27,000 real nuclear weapons in the United States, Russia and other states, and that many of these are on hair-trigger alert.
Nor do the ministers seem to realize that the determination they express to reduce the nuclear threat is diminished by their failure to take seriously their commitment, made within the framework of the NPT, to move toward the reduction and elimination of their own nuclear arsenals.
The stagnation in global disarmament is only part of the picture. In the United States, military authorities want new types of nuclear weapons; in Britain, the government is considering the replacement, at tremendous cost, of one generation of nuclear weapons by another - as defense against whom?
Last year a UN summit of heads of states and governments failed to adopt a single recommendation on how to attain further disarmament or prevent the proliferation of weapons of mass destruction. For nearly a decade, work at the disarmament conference in Geneva has stood still. It is time for a revival.
One can well understand that policymakers in the United States, as elsewhere, feel disappointment and concern that the global instruments against nuclear proliferation - the NPT and international inspection - have proved to be insufficient to stop Iraq, North Korea, Libya and possibly Iran on their way to nuclear weapons.
This may help explain their inclination to use the enormous military potential of the U.S. as either a threat or a direct means of preventing proliferation.
However, after three years of a costly and criticized war in Iraq to destroy weapons that did not exist, doubts are beginning to arise about the military method, and a greater readiness may emerge to try global cooperation once again to reduce and eventually eliminate weapons of mass destruction.
A report with 60 concrete recommendations to the states of the world on what they could do to free themselves from nuclear, biological and chemical weapons, worked out by an independent international commission of which I was the chairman, is now available at www.wmdcommission.org.
Apart from proposals for measures to prevent the spread of weapons of mass destruction to more states and terrorists, the report points to two measures that could turn current concerns about renewed arms races into new hopes for common security. In both cases, success would depend on the United States.
A U.S. ratification of the comprehensive test-ban treaty would, in all likelihood, lead other states to ratify and bring all such tests to an end, making the development of nuclear weapons more difficult. Leaving the treaty in limbo, as has been done since 1996, is to risk new weapons testing.
The second measure would be to conclude an internationally verified agreement to cut off the production of highly enriched uranium and plutonium for weapons purposes.
This would close the tap everywhere for more weapons material and would be of special importance if an agreement on nuclear cooperation with the United States were to give India access to more uranium than it has at the moment.
It is positive that the U.S. has recently presented a draft cutoff agreement, but hard to understand why this agreement does not include international inspection. Do the drafters think that the recent record of national intelligence indicates that international verification is superfluous?
--Tom Hayes